DDoS Protection Needs To Be Verified and Measured
DDoS attacks can severely cripple business-critical applications and bring business operations down, impacting revenues and the brand. They put large strains on companies' global networks and their upstream ISP networks. Cloud-based Distributed Denial of Service (DDoS) mitigation services or an on-site mitigation strategy are two methods employed by companies to stop or lessen these unpredictable attacks.
Both internal and external network visibility is essential to understanding and ensuring that your user experiences are not impacted in the event your network experiences a DDoS attack. The first step in remediation is for you to continuously identify potential DDoS threats that impact your users and secondly to monitor how effective your internal mitigation or cloud-based mitigation services are performing during these attacks. ThousandEyes DDoS monitoring performs both of these DDoS attack responses and visualizes the impacts, while recording performance data that can be shared in real-time with internal IT teams or external mitigation services personnel, enabling detailed collaborative forensics.
DDoS Mitigation Service Monitoring with ThousandEyes
ThousandEyes tracks the activation of a DDoS mitigation service using DNS or BGP to detect whether traffic is being routed as expected. Using ThousandEyes, you can measure whether deployed mitigation techniques are successful and identify specific devices or scrubbing centers that affect performance.
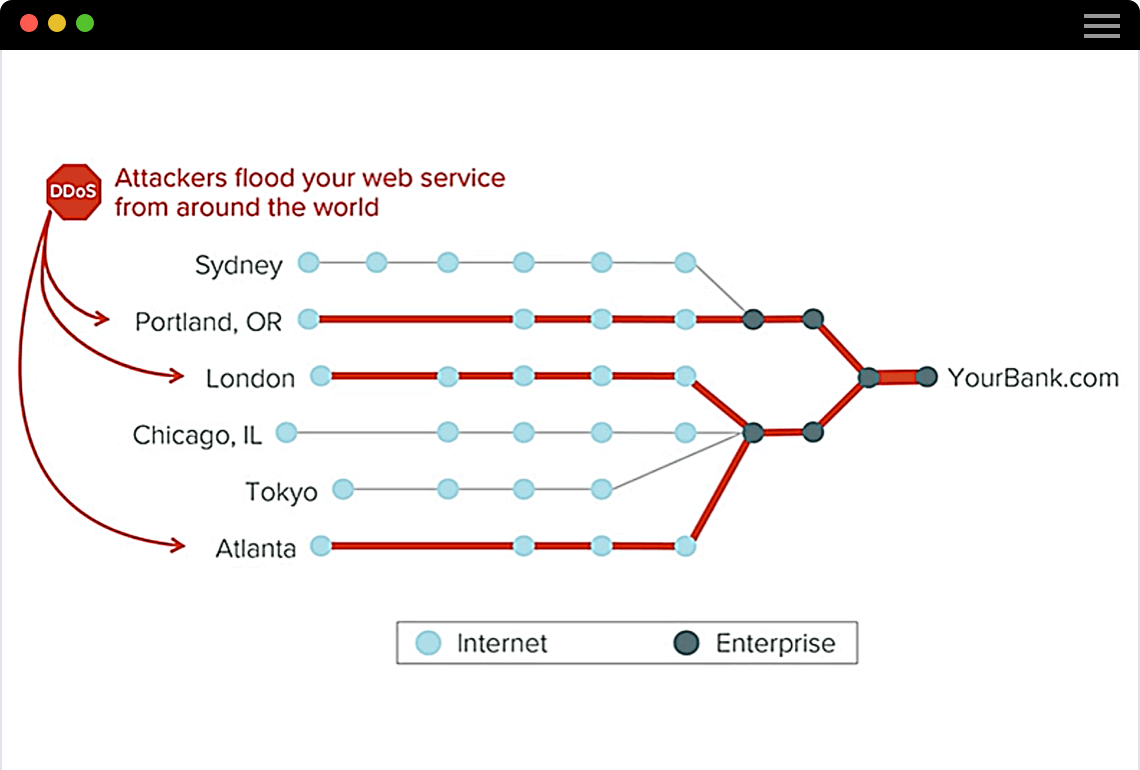
Understand DDoS Attacks From an Outside-In Visual Perspective
With ThousandEyes, network path visualization makes it possible to track a DDoS attack:
- Quickly locate packet loss, high latency links and overloaded scrubbing centers that impact your application performance
- Clearly track the impact of DDoS attacks to see what is being stressed: DNS, ISP networks, edge routers or an overloaded application server
- Identify underperforming elements within your cloud mitigation provider, such as overloaded scrubbing centers or misrouted traffic
- Easily correlate this information against baseline traffic behavior, compare time periods and save data for later forensics
Featured Blog Posts

Analyzing the Wikipedia DDoS Attack

Three Common Types of DDoS Attacks
Why ThousandEyes?
Track Performance of Your DDoS Mitigation Service
Verify the traffic handoff to your mitigation service with visibility into DNS and BGP.
Monitor DDoS Attacks
By tracking DDoS attacks, get deep insight into whether the mitigation techniques being used are working.
Speed Up Resolution
Collaborate with external ISPs and mitigation providers in real time to resolve any security issues
Explore ThousandEyes
Network & Application Synthetics
Start Monitoring your DDoS Mitigation Service
